If you’ve licensed Windows 10, you may have faced with a suggestion to upgrade to a new version of the OS 11. But this upgrade has several requirements for your PC, among which is the presence of a TPM module. Some may argue that you can do without it since the module can be expensive.
But many users would just like to know what it is and how to detect it on their computer. So I will provide you with information and help you understand what a TPM module is and how to detect it on your motherboard.
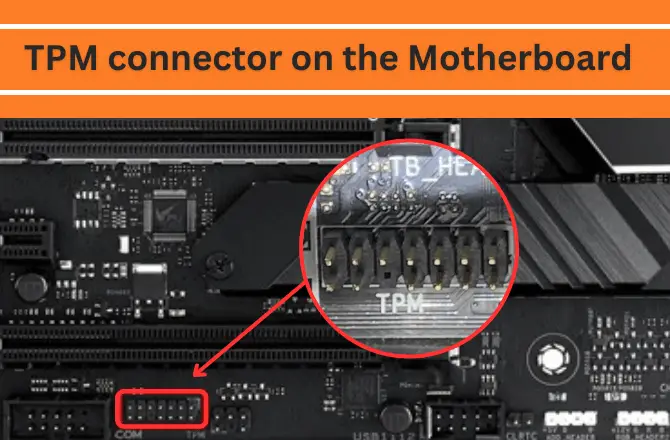
TPM connector on the Motherboard – What is it and What is it for?
So, TPM stands for “Trusted Platform Module“. It connects through a special port to the motherboard and provides encryption of the user’s personal data. The module stores information and transmits it, responds to commands.
In its composition:
- Secure I/O system.
- Special cryptographic processor.
- Memory that stores settings registers. She is energetic.
- Memory for storing the main encryption key, non-volatile.
Among the functions of this encryption device:
- Creation, storage and use of encryption keys.
- Authentication of PC components.
- OS integrity assessment.
- Additional protection against malware.
Sometimes the TPM Connector is useful as a component of an entire computer security system. For example, it is used to create a key that prevents malware from brute-force authentication of a user.
Where is TPM Located?
The module was initially integrated into the processor, because it does not have to be a separate chip, all its functions can be performed by special programs. But now it is still customary to separate them.
And therefore the TPM is either soldered directly to the motherboard or a connector is provided, allowing users to easily purchase and connect the chip. To find the connector for connecting the module, take a look at the edges of the motherboard where it’s most conveniently placed. If not, look for a small chip that says TPM.
How TPM Works?
It seems clear what it is – TPM, and what it is for, but it is not entirely clear how exactly it works. Cryptographic encryption sounds powerful, but let’s break it down in a more relatable way.
Imagine that you want to encrypt some data. This data, no matter how you see it, is defined by the computer as strings of characters. During encryption, these data strings are combined with a special additional string of characters, which sort of breaks the data structure. This string of characters is called the cryptographic key. Once encrypted, only the person with the key can use the data.
The system recognizes the key, determines which characters are superfluous, excludes them from processing, and you get clean information. But a system without a key will not be able to determine whether there are extra characters or not, and then it will be impossible to read any data.
So, in a nutshell, encryption keeps your data safe and secure, allowing only authorized individuals to access it.
In Windows 11
With the release of Windows 11, Microsoft announced new security measures for their operating systems. And one of the prerequisites for ensuring this security was the presence of a TPM on the motherboard. But this measure is necessary until Microsoft’s new “Pluton” security chip is integrated into processors.
In Windows 11, the TPM module plays a pivotal role in the security system and passwords, especially if you’re using the PRO or Enterprise version where you can run BitLocker. This program encrypts the entire disk and stores the key within the TPM. In the Home version, Device Encryption does about the same thing. The module also improves the operation of Device Guard and helps Windows network services.
By prioritizing these security measures, Microsoft is dedicated to providing a safer and more reliable computing experience for all Windows.
What’s new in TPM 2.0?
To support Windows 11, the computer will need a version 2.0 device, so if you have a previous one, 1.2, it would be necessary to upgrade to the more modern 2.0 version, because its encryption method is more secure, based on elliptic curves. And here 256-bit SHA-2 hashes are generated instead of 160-bit SHA-1 as it was before.
Additionally, it’s important to note that the 2.0 module is designed to work with the new UEFI BIOS, which offers improved support for secure OS boot or POST.
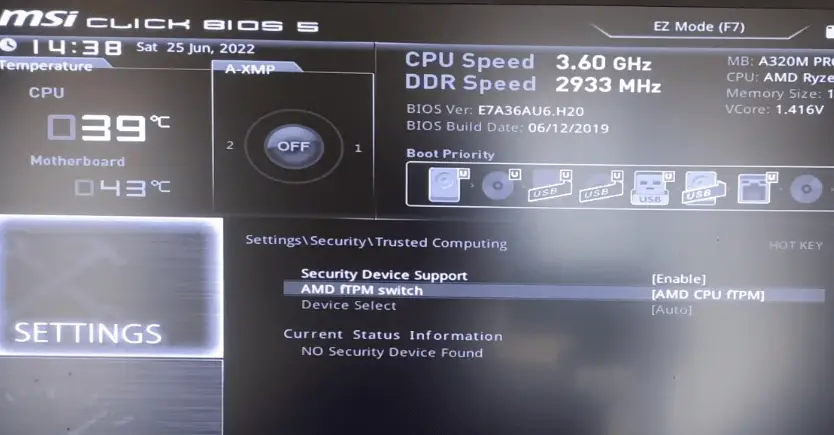
How to check TPM version in BIOS
If suddenly you find that an already installed or completely new module is not displayed in the system, you can enable it in the BIOS. First you need to get into the BIOS by pressing the correct key combination like DEL, Fn Key while boot loading when you restart PC for your board such as MSI, Asus or Gigabyte.
Once you’re in the BIOS, navigate to a section like “Security” or “Advanced”. In there, you’ll find options to enable features like TPM Device, Security Device, Security Chip, and also view its version.
Can I Install TPM to my motherboard?
In theory, you can just take and connect the TPM connector to the motherboard, if it has the appropriate socket. In this case, the version of the device itself does not matter, so it will not be difficult to replace one with another.
If your motherboard does not have a TPM header: In this case, you generally can’t add a TPM module to the motherboard form factor. However, starting from Intel’s 8th generation chips and AMD’s Ryzen chips, these CPUs have a firmware TPM (fTPM) built into them. This provides the same functionality as a hardware TPM, and it’s usually just a matter of enabling it in the BIOS/UEFI settings.
Another thing is if you have a laptop. There, this module is often soldered into the motherboard itself. Therefore, you don’t need to think about how to install this device yourself – only a specialist can do this.
Is the TPM module enabled in the BIOS or in Windows?
In BIOS, this can be done if you find a device in a section like “Security” or “Advanced” and set it to “On” or “Available” or “Enable”.
To check if this encryption module is enabled in Windows 10 settings, you need to proceed as follows:
- Go to “Start”.
- Open “Options”.
- Select “Update and Security”.
- Then click on “Windows Security”.
- Open Device Security.
Here, you’ll find a “Security Handler” section where it will say that the TPM is protecting your data. This means that the module is enabled. If there is no such section, then the module is either disabled or missing. By the way, you can also check the version of the module determined by the system. Simply click on “Information about the security handler” within the same window.
Do I need to configure something?
In theory, you do not need to configure anything, since the drivers are installed by themselves. But sometimes it may be necessary to clear it in order to assign a new owner. This can be done using the built-in Windows tools:
- Press Win+R.
- Enter “tpm.msc” into the window.
- When the desired window opens, on the right side of the list, you can select “Clear TPM”.
- Click and follow the instructions.
If you suspect that the drivers are crooked, go to the “Device Manager”. This can be done by pressing Win+R and then typing “devmgmt.msc”. Here in “Security devices” will be your device. You can right-click on it, open Properties, and like any other device, update the drivers or uninstall them.
If you find “Compatible TPM cannot be found” this means that your system does not support the TPM drivers.
- Read Also: What are the Front Panel Connectors on the Case?
- Related: Can A Power Outage Damage A PC?
What are the Problems with TPM?
Of course, for some users, the main problem with TPM is its requirement for Windows 11 installation. Because most often a PC can pull a new OS anyway, and you don’t really want to buy a not the cheapest part just to try Windows 11.
There are those who, at first glance, do not like the TPM module itself. While it does provide protection, it may not be flawless and there are instances where it may seem powerless. Some even view it as more of a tracking device than a helpful assistant.
It’s important to note that there is a always a chance that the OS will check the publishers of “suspicious” applications through TPM or completely close some program for use if its publisher ends support. And due to the incorrect operation of the module, you can lose access to some applications, for example, office programs.
But today such seems like discussions about this topic have lost some popularity lately, and many have resigned themselves to the need for a module. Now you will know a little more about your PC and its security.
I will talk more about motherboards and other computer components, and in order not to miss anything, stay connected!



thank you so much
i couldnt connect to wifi with my pc. for many months i tried everything but no use.
until tonight i see this article and step 5 did the magic
thanks so much again
Mehdi, Glad to listen that!